ISO 7816-4 spy using Wireshark
In a previous blog article "CCID USB spy using Wireshark" I documented how to use Wireshark to analyse USB CCID packets.
It is also possible to continue the packet decoding to show ISO 7816-4 format commands.
Raw USB packets
By default you will get USB packets.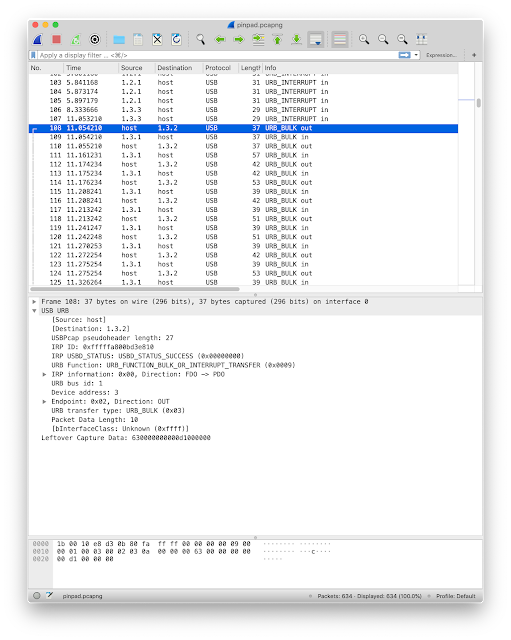
CCID packets
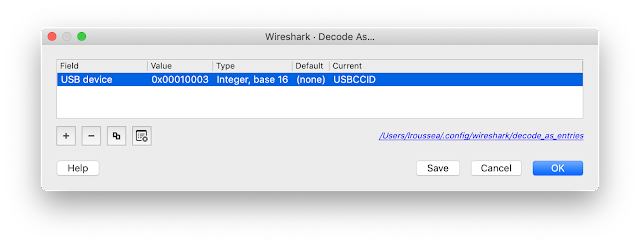
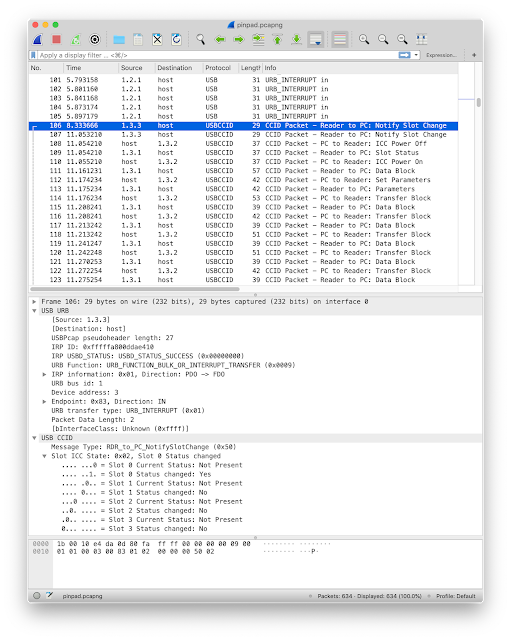
Enable the USBCCID decoder in the Wireshark menu Analyze -> Decode as...You will then see CCID packets.
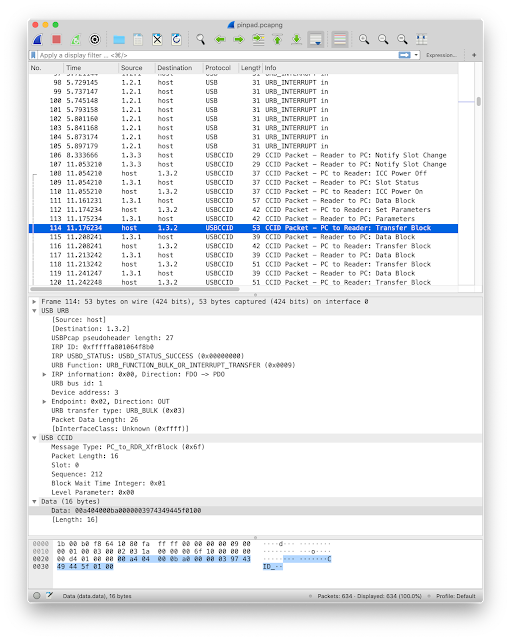
But APDUs sent to the reader may be hard to read is you do not decode ISO 7816-4 directly in your head.
All we get here is Data:
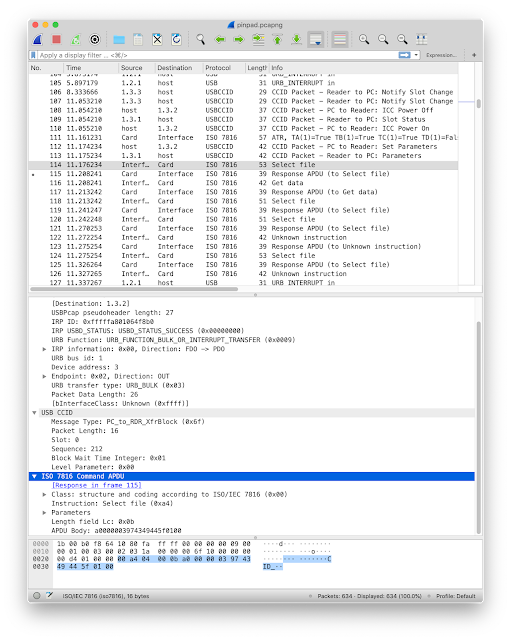
00 a4 04 00 0b a0 00 00 03 97 43 49 44 5f 01 00ISO 7816 commands
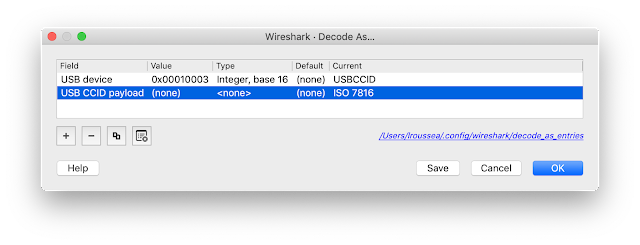
Now enable the ISO 7816 decoder.And you will see ISO 7816-4 command names.
Here you see that the APDU
00 a4 04 00 0b a0 00 00 03 97 43 49 44 5f 01 00 is a "Select file" (the second byte, INS byte, is 0xA4)Limitations
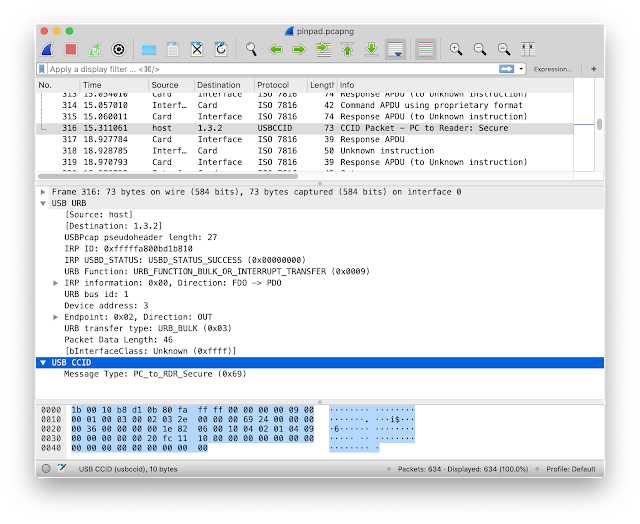
Not all the CCID packets are decoded.For example the Secure command (0x69) is not (yet) decoded.
Only the first CCID byte is decoded as "Message Type: PC_to_RDR_Secure (0x69)". The remaining of the CCID frame is not decoded. And this command is not easy to decode by hand without the CCID specification.
This CCID Secure command is used with a pinpad reader to make the user enter its PIN code in the pinpad and not on the computer keyboard. See here for a list of pinpad readers working with my CCID driver.
The Secure command uses parameters to set the PIN padding, the messages displayed to the user, the min and max PIN lengths, the validation conditions and some other parameters. Not all pinpad readers support the same set of parameters so the situation is complex.
Windows support
In my previous article "CCID USB spy using Wireshark" I make the USB trace acquisition on a GNU/Linux system.This time I made the capture on Windows, saved the file on disk (.pcapng format) and used Wireshark on macOS to study the file. Yes, I prefer to NOT use Windows as much as possible.
So whatever the system you are using (GNU/Linux, macOS or Windows, and maybe others) Wireshark can help you.