CCID USB spy using Wireshark
Sometimes you need to know exactly what is happening at the USB level. You have two options:
- use a hardware USB analyzer
- use a software USB analyzer
Wireshark
Since some time, it is possible to use the wonderful Wireshark program to display and analyze USB frames. Wireshark is mainly used for analyzing network packets but it is also possible to display USB packets. Wireshark is even able to display the CCID commands inside the USB packets.
How-to
A documentation is available at USB capture setup and also at Capturing USB data through Wireshark.This article describes what I did.
Setup the kernel
You first need to load the usbmon kernel module.$ sudo modprobe usbmon
tshark (a command line tool) should now be able to capture on usbmon interfaces. Check it using:$ tshark -D 1. eth0 2. any 3. lo (Loopback) 4. nflog 5. nfqueue 6. usbmon1 7. usbmon2
In my case I have 2 USB buses labeled usbmon1 and usbmon2.
Capture the USB frames
Before capturing the USB frames you need to know on which USB bus is connected your device.Identify the device USB bus
$ lsusb Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub Bus 002 Device 004: ID 08e6:3437 Gemplus GemPC Twin SmartCard Reader Bus 002 Device 002: ID 80ee:0021 VirtualBox USB Tablet Bus 002 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
In my case the device I want to study is on the bus 002 so I will use usbmon2.
Start the capture
$ tshark -i usbmon2 -w trace1.pcap Capturing on 'usbmon2' tshark: The capture session could not be initiated on interface 'usbmon2' (Can't open USB bus file /sys/kernel/debug/usb/usbmon/2t: Permission denied). Please check to make sure you have sufficient permissions, and that you have the proper interface or pipe specified.
For security reasons
tshark refuses to be run as root. So I needed to change some file access rights.$ sudo chmod +rx /sys/kernel/debug/ $ sudo chmod a+rw /sys/kernel/debug/usb/usbmon/2t
Then (re)start tshark and use Ctrl-C to stop after some traffic has been captured.
$ tshark -i usbmon2 -w trace1.pcap Capturing on 'usbmon2' 1270 tshark: Can't get packet-drop statistics: Can't open USB stats file /sys/kernel/debug/usb/usbmon/2s: Permission denied Please report this to the Wireshark developers. http://bugs.wireshark.org/ (This is not a crash; please do not report it as such.)
Capture analysis
The filetrace1.pcap contains the USB frames and can be displayed using the graphical interface of Wireshark.Enable the CCID decoder
Unless you can read the CCID protocol from hexadecimal, it is a good idea to tell Wireshark to decode the USB frames as USBCCID.Go in the menu "Analyze" -> "Decode as..." and select USBCCID in the dialog.
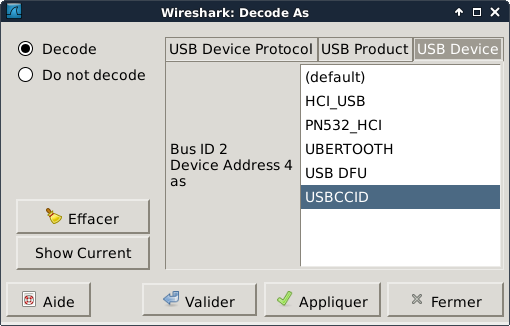
Wireshark will then display the USB frames with nice CCID names:
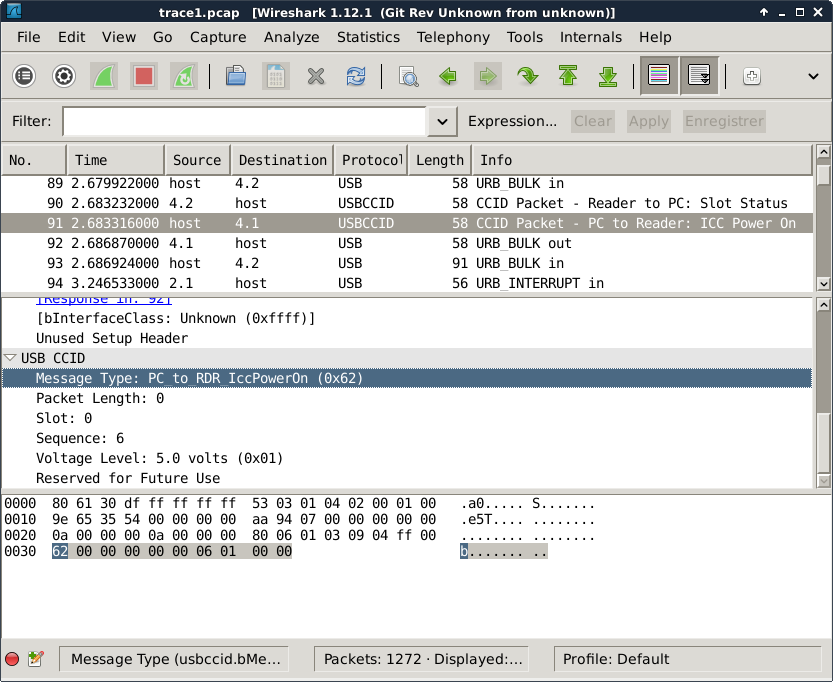
Here you can see a CCID Power On command.
- The command name is displayed in the top window: "Packet - PC to Reader: ICC Power On"
- And the content of the command (the 10 last bytes specific to CCID) are documented in the lower window: "Message Type: PC_to_RDR_IccPowerOn (0x62)", etc.
I do not expect every one to use Wireshark to look at CCID frames. But if you have a problem with a CCID reader and wants to know exactly what is happening Wireshark can help you for a very very limited budget (Wireshark is a free software under GNU GPL v2 license).
This blog article is also a way for me to document how to do it for the next time :-)
Conclusion
Wireshark is a great tool.Linux is a great kernel.
Debian GNU/Linux is a great operating system.