ATR statistics: T0 - Format byte
Article from the series "ATR statistics"
T0 - Format byte
The ISO 7816-3 specification is not public. So I can't copy/paste part of the text. I will use Wikipedia instead.From Wikipedia https://en.wikipedia.org/wiki/Answer_to_reset#Format_byte_T0:
Format byte T0
The Format byte T0 encodes in its 4 low-order bits (4th MSbit to 1st LSbit) the number K of historical bytes Ti, in range [0..15].
It also encodes in its 4 high-order bits the presence of at most 4 other interface bytes: TA1 (resp. TB1, TC1, TD1) follow, in that order, if the 5th (resp. 6th, 7th, 8th) bit of T0 is 1.
| T0 | # | % |
|---|---|---|
| 0xFF | 160 | 7.72 % |
| 0x9F | 145 | 7.00 % |
| 0x8F | 108 | 5.21 % |
| 0x6F | 101 | 4.87 % |
| 0x7F | 87 | 4.20 % |
| 0x6E | 82 | 3.96 % |
| 0x65 | 58 | 2.80 % |
| 0x9E | 51 | 2.46 % |
| 0x7D | 45 | 2.17 % |
| 0x67 | 43 | 2.08 % |
| 0xEF | 40 | 1.93 % |
| 0x88 | 37 | 1.79 % |
| 0x6D | 31 | 1.50 % |
| 0xFD | 28 | 1.35 % |
| 0x3F | 25 | 1.21 % |
| 0xFA | 25 | 1.21 % |
| 0x68 | 24 | 1.16 % |
| 0x04 | 23 | 1.11 % |
| 0x3B | 22 | 1.06 % |
| 0x85 | 22 | 1.06 % |
| 0xF7 | 22 | 1.06 % |
| 0xDB | 21 | 1.01 % |
| 0xBE | 20 | 0.97 % |
| 0xBF | 20 | 0.97 % |
| 0x16 | 19 | 0.92 % |
| 0x6B | 19 | 0.92 % |
| 0x8C | 19 | 0.92 % |
| 0xDF | 19 | 0.92 % |
| 0xFB | 19 | 0.92 % |
| 0x8A | 18 | 0.87 % |
| 0xF9 | 17 | 0.82 % |
| 0x1F | 16 | 0.77 % |
| 0x66 | 16 | 0.77 % |
| 0x69 | 16 | 0.77 % |
| 0x7E | 16 | 0.77 % |
| 0x89 | 16 | 0.77 % |
| 0x78 | 15 | 0.72 % |
| 0x95 | 15 | 0.72 % |
| 0xFE | 15 | 0.72 % |
| 0x17 | 13 | 0.63 % |
| 0x77 | 13 | 0.63 % |
| 0x8E | 13 | 0.63 % |
| 0xDD | 13 | 0.63 % |
| 0xF8 | 13 | 0.63 % |
| 0x2F | 12 | 0.58 % |
| 0x6A | 12 | 0.58 % |
| 0x6C | 12 | 0.58 % |
| 0x86 | 12 | 0.58 % |
| 0x8B | 12 | 0.58 % |
| 0xE9 | 12 | 0.58 % |
| 0x7A | 11 | 0.53 % |
| 0x98 | 11 | 0.53 % |
| 0x9A | 10 | 0.48 % |
| 0x9D | 10 | 0.48 % |
| 0xBA | 10 | 0.48 % |
| 0x27 | 9 | 0.43 % |
| 0x82 | 9 | 0.43 % |
| 0x87 | 9 | 0.43 % |
| 0xBC | 9 | 0.43 % |
| 0xE6 | 9 | 0.43 % |
| 0x06 | 8 | 0.39 % |
| 0x19 | 8 | 0.39 % |
| 0x2A | 8 | 0.39 % |
| 0x7B | 8 | 0.39 % |
| 0x84 | 8 | 0.39 % |
| 0xF2 | 8 | 0.39 % |
| 0xFC | 8 | 0.39 % |
| 0x0F | 7 | 0.34 % |
| 0x26 | 7 | 0.34 % |
| 0x3D | 7 | 0.34 % |
| 0x75 | 7 | 0.34 % |
| 0x79 | 7 | 0.34 % |
| 0xB7 | 7 | 0.34 % |
| 0xD5 | 7 | 0.34 % |
| 0xEA | 7 | 0.34 % |
| 0xF5 | 7 | 0.34 % |
| 0x15 | 6 | 0.29 % |
| 0x23 | 6 | 0.29 % |
| 0x3C | 6 | 0.29 % |
| 0x76 | 6 | 0.29 % |
| 0xA7 | 6 | 0.29 % |
| 0x02 | 5 | 0.24 % |
| 0x24 | 5 | 0.24 % |
| 0x8D | 5 | 0.24 % |
| 0xB2 | 5 | 0.24 % |
| 0xE2 | 5 | 0.24 % |
| 0xE8 | 5 | 0.24 % |
| 0xEE | 5 | 0.24 % |
| 0x05 | 4 | 0.19 % |
| 0x18 | 4 | 0.19 % |
| 0x7C | 4 | 0.19 % |
| 0x9C | 4 | 0.19 % |
| 0xB3 | 4 | 0.19 % |
| 0xD9 | 4 | 0.19 % |
| 0xDC | 4 | 0.19 % |
| 0xDE | 4 | 0.19 % |
| 0xE7 | 4 | 0.19 % |
| 0xF0 | 4 | 0.19 % |
| 0xF6 | 4 | 0.19 % |
| 0x07 | 3 | 0.14 % |
| 0x12 | 3 | 0.14 % |
| 0x1B | 3 | 0.14 % |
| 0x1D | 3 | 0.14 % |
| 0x29 | 3 | 0.14 % |
| 0x37 | 3 | 0.14 % |
| 0x3E | 3 | 0.14 % |
| 0x5F | 3 | 0.14 % |
| 0x64 | 3 | 0.14 % |
| 0x97 | 3 | 0.14 % |
| 0x99 | 3 | 0.14 % |
| 0x9B | 3 | 0.14 % |
| 0xB9 | 3 | 0.14 % |
| 0xBB | 3 | 0.14 % |
| 0xBD | 3 | 0.14 % |
| 0xD2 | 3 | 0.14 % |
| 0xD6 | 3 | 0.14 % |
| 0xEC | 3 | 0.14 % |
| 0xED | 3 | 0.14 % |
| 0xF4 | 3 | 0.14 % |
| 0x0A | 2 | 0.10 % |
| 0x32 | 2 | 0.10 % |
| 0x34 | 2 | 0.10 % |
| 0x5B | 2 | 0.10 % |
| 0x81 | 2 | 0.10 % |
| 0x83 | 2 | 0.10 % |
| 0x90 | 2 | 0.10 % |
| 0x96 | 2 | 0.10 % |
| 0xA8 | 2 | 0.10 % |
| 0xAA | 2 | 0.10 % |
| 0xAC | 2 | 0.10 % |
| 0xB0 | 2 | 0.10 % |
| 0xB8 | 2 | 0.10 % |
| 0xD8 | 2 | 0.10 % |
| 0xDA | 2 | 0.10 % |
| 0xE0 | 2 | 0.10 % |
| 0xE5 | 2 | 0.10 % |
| 0xEB | 2 | 0.10 % |
| 0x00 | 1 | 0.05 % |
| 0x09 | 1 | 0.05 % |
| 0x0E | 1 | 0.05 % |
| 0x1C | 1 | 0.05 % |
| 0x1E | 1 | 0.05 % |
| 0x28 | 1 | 0.05 % |
| 0x2D | 1 | 0.05 % |
| 0x57 | 1 | 0.05 % |
| 0x5E | 1 | 0.05 % |
| 0x63 | 1 | 0.05 % |
| 0x74 | 1 | 0.05 % |
| 0x80 | 1 | 0.05 % |
| 0x91 | 1 | 0.05 % |
| 0x94 | 1 | 0.05 % |
| 0xAB | 1 | 0.05 % |
| 0xAD | 1 | 0.05 % |
| 0xD0 | 1 | 0.05 % |
| 0xE3 | 1 | 0.05 % |
| 0xF3 | 1 | 0.05 % |
Doing statistics on the complete T0 byte is not really informative.
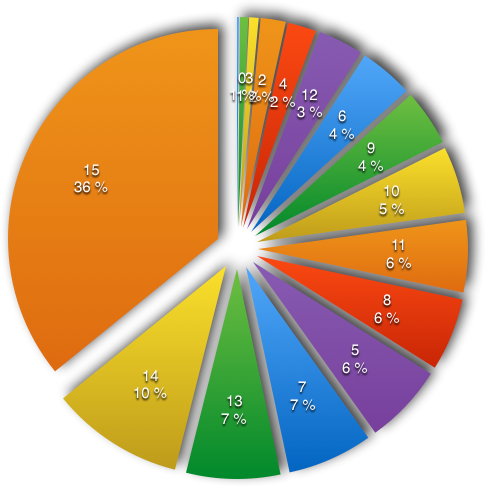
Interface nibble
| format | # | % |
|---|---|---|
| 1 | 3 | 0.14 % |
| 0 | 13 | 0.63 % |
| 3 | 15 | 0.72 % |
| 2 | 40 | 1.93 % |
| 4 | 46 | 2.22 % |
| 12 | 72 | 3.47 % |
| 6 | 86 | 4.15 % |
| 9 | 90 | 4.34 % |
| 10 | 107 | 5.16 % |
| 11 | 115 | 5.55 % |
| 8 | 116 | 5.60 % |
| 5 | 128 | 6.18 % |
| 7 | 136 | 6.56 % |
| 13 | 150 | 7.24 % |
| 14 | 212 | 10.23 % |
| 15 | 743 | 35.86 % |
Interpretation
In 36% of the ATRs the LSB is equal to 15 (or 1111b in binary) indicating that TA1, TB1, TC1, TD1 are present.For 10% of ATRs the LSB is equal to 14 (or 1110b in binary) indicating that TB1, TC1, TD1 are present, and TA1 is not present.
For 0.63% of ATRs the LSB is equal to 0 (or 0000b in binary) indicate that TA1, TB1, TC1, TD1 are all absent.
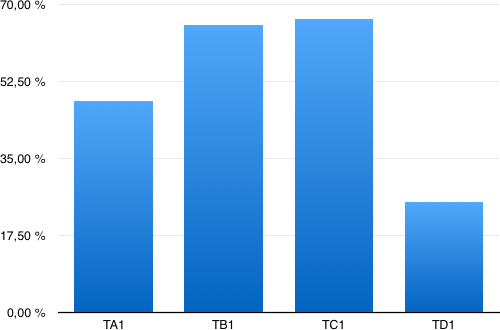
A better way to display the result is to isolate TA1, TB1, TC1, TD1 and count them independently.
| interface | # | % |
|---|---|---|
| TA1 | 996 | 48.07 % |
| TB1 | 1355 | 65.40 % |
| TC1 | 1381 | 66.65 % |
| TD1 | 519 | 25.05 % |
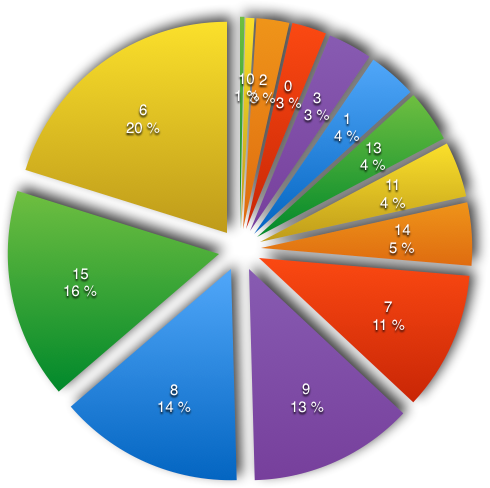
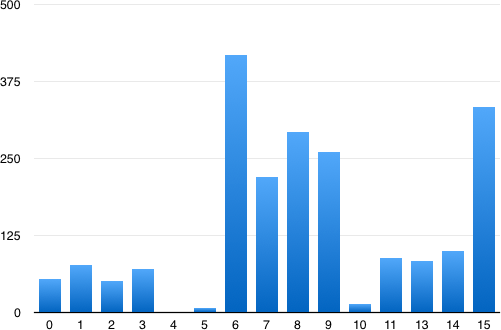
Historic nibble
| historic | # | % |
|---|---|---|
| 4 | 0 | 0.00 % |
| 5 | 7 | 0.34 % |
| 10 | 14 | 0.68 % |
| 2 | 52 | 2.51 % |
| 0 | 55 | 2.65 % |
| 3 | 70 | 3.38 % |
| 1 | 77 | 3.72 % |
| 13 | 83 | 4.01 % |
| 11 | 88 | 4.25 % |
| 14 | 100 | 4.83 % |
| 7 | 220 | 10.62 % |
| 9 | 261 | 12.60 % |
| 8 | 293 | 14.14 % |
| 15 | 334 | 16.12 % |
| 6 | 418 | 20.17 % |
The number of historic bytes is not equally distributed between 0 and 15 bytes. I guess that is because the historic bytes are coded using a TLV format so some sizes are more frequent than others.
Update: 22th March 2020
It looks like the data for the Historic nibble are wrong. You can get correct values in the article "ATR statistics: Historical bytes - Historical bytes Ti (optional)".Sorry for that mistake.